Identifying fraudulent "phishing" email
"Phishing" (also known as "carding" or "spoofing") refers to email that attempts to fraudulently acquire personal information from you, such as your account password or credit card information. On the surface, the email may appear to be from a legitimate company or individual, but it's not.
As a general rule, never send credit card information, account passwords, or extensive personal information in an email unless you verify that the recipient is who they claim to be. Many companies have policies that state they will never solicit such information from customers by email.
If you do receive email that you're not sure is valid, here are some tips that can help you determine its legitimacy.
Find out who the email is really from
View the email headers to see where the message really originated from. To find out how to view headers in OS X Mail, see this article. If you're using iCloud Mail on the web (webmail), follow these steps to view the headers.
A typical email header displays several lines that begin with "Received." Note the last "Received" line; this line will look something like this:
Received from genericwebsite.org (123.456.789.101)
If the "Received from" information does not match the email address of the sender or the company being represented in the email, it usually means that the message did not truly come from that individual or company.
Be cautious of links in the email
Note: Apple may send email notifications to you containing embedded links to legitimate third-party sites. When you receive an email with links to other sites, use the information below to help you determine whether or not the links are legitimate.
One common phishing technique is to include links in an email that look like they go to a legitimate website. Upon closer inspection, the link may actually take you to a website that has nothing to do with the company the email is pretending to be from, even though the resulting website may be designed to look exactly the same.
In OS X Lion and Mountain Lion, Mail can help identify these type of links. Simply mouse over (but don't click) any link in an email, and you will see a pop-up that shows you the actual URL that you will be taken to. Here's an example:
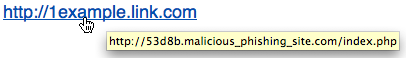
You can clearly see that the visible link and the real link do not match—be careful. If the URLs in your email do not match, or the second URL is not from a domain or company you are familiar with, this is a good indication that this is a phishing email.
Tip: If you're using iCloud Mail with Safari, you can mouse over any link and compare the addresses there as well. If you have the Status Bar enabled in your browser, mousing over a link will show the URL in the browser's Status Bar at the bottom of the window.
Check that the website you're accessing is legitimate
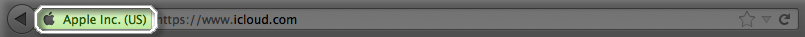
If you think the URL is legitimate and you click on the link, you can still check that it's a trusted website and business. Modern browsers like Safari 5, Firefox 7, Google Chrome, and Internet Explorer 10 display the company name in green if the site has been issued an Extended Validation (EV) Certificate and is a legitimate website/business.
The iCloud service uses EV Certificates. Just look at the address bar in your web browser when you log in to iCloud.com. You will see "Apple, Inc." displayed in green, so you know that the site is legitimately Apple:
Safari

Firefox
Note the email greeting
Phishing emails tend to start with generic phrases like "Dear valued customer" or your email account name, such as "Dear snookums123," instead of your name ("Dear Emily" for example). Most legitimate companies include your name in their correspondence because companies will have it on record (if you've dealt with them before).
The message arrived at a different email address than the one you gave the sender
If the sender sent the message to an address that was not the one you provided to the company, this is usually a good indication that the message is not legitimate. You can usually verify what email address a company has on file on their website (just be sure to go to their real website instead of following any links in a suspicious email).
Keep previous history in mind
If you've had previous, valid correspondence with the company, compare those messages to the email in question. If you have never done business with a particular company, and you receive an email that appears to be from that company requesting account information, it could be an attempt at phishing. Again, never email account information or credit card information if you are in doubt.
Never provide personal account information through email
f you receive an unsolicited commercial email requesting personal information, do not provide any information without first checking directly with the company that appears to be the one requesting this information. Do not reply to the message or click any of the links in the message. Instead, visit the company's website and find an email address to contact regarding this issue, or call the company. Many companies appreciate being notified about fraudulent attempts to gain information about their customers.
Be cautious of attachments
If you receive an unsolicited message that contains an attachment, do not open it. Contact the company directly to verify the contents of the email and the attachment before opening it.
What to do with suspicious iCloud emails
If you receive a suspicious email, select the message text so that it is highlighted. Choose Forward as Attachment from the Message menu (OS X Mail) or the Actions menu (Outlook). Send the email to abuse@icloud.com. This provides Apple's legal department and law enforcement with useful information to help prevent future phishing emails.
Note: For suspicious emails related to iTunes, see this article.
^ed

thanks for useful information
ReplyDeleteThanks for information regarding technical issue we face. How they are resolvable with the help of an Apple support team
ReplyDelete