AT&T and Verizon want to manage your identity across websites and apps
Carriers' "Project Verify" would use your phone as authentication device.
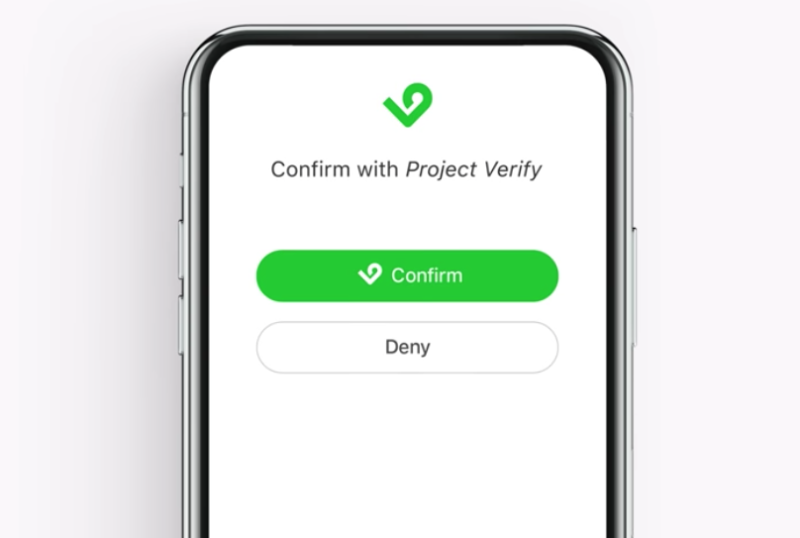
The four major US mobile carriers have unveiled a system that would let them manage your logins across any third-party website or app that hooks into it.
"Project Verify" from a consortium of AT&T, Verizon Wireless, T-Mobile US, and Sprint, was unveiled in a demo yesterday. It works similarly to other multi-factor authentication systems by letting users approve or deny login requests from other websites and apps, reducing the number of times users must enter passwords. The carriers' consortium is putting the call out to developers of third-party apps and websites, who can contact the consortium for information on linking to the new authentication system.
"The Project Verify app can be preloaded or downloaded to the user's mobile device," a video describing the technology says. "And then when they face a login screen on their favorite sites and apps, they select the verify option. That's it—Project Verify does the rest."
The carriers hope to launch Verify next year.
Introducing Project Verify.
The carrier system would verify each person's identity with "a multi-factor profile based around the user's personal mobile device," taking into account the user's phone number, account tenure, IP address, phone account type, and SIM card details. The system "combines the carriers' proprietary, network-based authentication capabilities with other methods to verify a user's identity," the carriers say.
Users would be able to log in to Project Verify-linked sites or apps by selecting the verify option within those apps or sites. The Project Verify app would let them manage which sites and apps are linked to their mobile identity.
Is this a good idea?
But do you want your carrier managing your logins across the websites and apps you use on your phone? AT&T, Verizon, T-Mobile, and Sprint aren't exactly the tech industry's best protectors of security and privacy.
The four major carriers were recently caught leaking the real-time location of most US cell phones. After facing pressure from Sen. Ron Wyden (D-Ore.), the carriers agreed to stop selling their mobile customers' location information to third-party data brokers.
The carriers don't face any major rules preventing them from misusing their customers' Web-browsing and app-usage data. Last year, the mobile carriers and other Internet providers convinced Congress and President Trump to prevent implementation of rules that would have forced them to get customers' opt-in consent before using, sharing, or selling their browsing and app-usage histories for advertising purposes.
"I don't trust the carriers"
There are good reasons to be skeptical of the carriers' ability to securely manage logins, security reporter Brian Krebs wrote yesterday.
"A key question about adoption of this fledgling initiative will be how much trust consumers place with the wireless companies, which have struggled mightily over the past several years to validate that their own customers are who they say they are," Krebs wrote. He continued:
All four major mobile providers currently are struggling to protect customers against scams designed to seize control over a target's mobile phone number. In an increasingly common scenario, attackers impersonate the customer over the phone or in mobile retail stores in a bid to get the target's number transferred to a device they control. When successful, these attacks—known as SIM swaps and mobile number port-out scams—allow thieves to intercept one-time authentication codes sent to a customer's mobile device via text message or automated phone call.
AT&T VP Johannes Jaskolski, who is managing the carriers' Project Verify consortium, told Krebs that the system will not centralize subscriber data into a multi-carrier database.
"We're not going to be aggregating and centralizing this subscriber data, which will remain with each carrier separately," Jaskolski said. Verify "will be portable by design and is not designed to keep a subscriber stuck to one specific carrier." It will let the user maintain "control of whatever gets shared with third parties," he added.
But Krebs is still skeptical, and so is security researcher Nicholas Weaver of the International Computer Science Institute at UC Berkeley. Krebs paraphrased Weaver as saying that "this new solution could make mobile phones and their associated numbers even more of an attractive target for cyber thieves."
"The carriers have a dismal track record of authenticating the user," Weaver also said. "If the carriers were trustworthy, I think this would be unequivocally a good idea. The problem is I don't trust the carriers."

No comments:
Post a Comment